[vc_row css=”.vc_custom_1452687555475{margin-bottom: 100px !important;}”][vc_column offset=”vc_col-lg-9 vc_col-md-9″ css=”.vc_custom_1452702342137{padding-right: 45px !important;}”][vc_custom_heading source=”post_title” use_theme_fonts=”yes” el_class=”no_stripe”][stm_post_details][vc_column_text css=”.vc_custom_1587669146554{margin-bottom: 20px !important;}”]During the past couple of weeks cybercriminals have wasted no time in exploiting the Covid crisis. Phishing attacks that try to trick users into clicking on a link to a bad website have increased tenfold.
The sudden transition to working from home means more scope for mistakes due to employees adjusting to a new environment and more opportunity for cybercriminals hoping to trick employees info giving over passwords and other important information.
Cybercriminals are leveraging the widespread use of Office 365 to steal account credentials. They also frequently put forwarders onto email accounts once they have gained entry to watch every email someone sends, waiting for their opportunity to strike.
Introducing 365 Protect
[/vc_column_text][vc_empty_space][vc_single_image image=”8200″ img_size=”600×400″ alignment=”center”][vc_empty_space][vc_column_text]We are taking our clients Office 365 security to the next level, adding to our advanced email protection and automated backup solutions. Our brand new set of surveillance tools are now also automatically included in our client’s plans will constantly scan all Office 365 accounts to make sure nothing untoward is going on and if anything is spotted, it can be stopped rapidly, before any damage is done, giving them huge peace of mind which is vital at the moment.
In effect, we are placing a guard dog at the entrance of your Office 365. You can’t be with your staff, watching their every move, but with 365 Protect it’s even better. Nothing will get missed. Any attempt to access your Office 365 will throw up a warning that can be acted on.
What does 365 Protect actually do?
365 Protect constantly monitors your Office 365 so no damage can be done. So, even if one of your staff inadvertently gives away their password, this would be spotted and stopped in its tracks. It would flag as a suspicious login. We’d know and you’d know. Ultimate peace of mind.
365 Protect secures Office 365 in the following ways:
▶ Email forwarding Alerts
What it does: You, and us, are sent an email alert as soon as any forwarder is set up on your emails. The forwarder may be legitimate – you may,
for example, want Pam from accounts to have a copy of your emails whilst you are on holiday. With a simple click of a button contained within the email alert, you can accept or reject the forwarder. And don’t worry if you miss the email. It won’t stop sending to us or you until a response has been made.
Why you need it: Cybercriminals frequently put forwarders onto accounts once they have gained entry. You need to be able to get rid of these fast before any damage can be done. It would take a full-time knowledgeable member of staff all day/every day to do this for every email account you have. Do you have the resource/knowledge/time to do this?
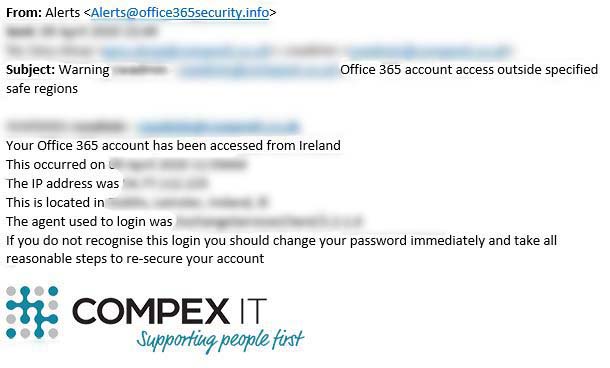
🗺Location Monitoring
What it does: 365 Protect alerts us as soon a login to your email account is spotted from a suspicious location.
Why you need it: Cybercriminals typically operate outside of the UK. You need to know instantly if your account is accessed from a suspicious location. Once we’re notified, we can immediately take steps to make sure no damage is done.
🔒Admin Monitoring
What it does: This clever tool makes sure you (and us) are notified when any new admin account/admin changes are made in your Office 365
accounts.
Why you need it: With an admin account, a cybercriminal can gain access to everything in your business, make changes, give permissions. They have the driving seat. You need to know who your admins are and be in control. It’s not just cybercriminals either, you need to know if your staff have made themselves an admin so you can remain in control of your business information and security.
🕵️♂️Spoofing Protection
What it does: We’re sure you’ve seen an email that looks like it has come from your colleague – it has their email address and looks very authentic, but they didn’t send it. Whenever an email is sent to you, this clever tool automatically checks for possible spoofing by running checks against the name and the domain. If it finds a match it lets you know by splashing a warning across the email.
Why you need it: You can’t be watching your staff all the time. It’s when you’re pushed for time, feeling distracted, tired, busy that you are most likely to click on a rogue email. We’ve seen it done time and time again. We’ve even seen it in our own business.
📊Security Report
What it does: The report reveals key information such as who your admins are, what forwarders are on your mailbox, who shares what mailbox, are there any external documents being shared and loads more. It keeps you in control and compliant.
Why you need it: We all need to be on the ball when it comes to being in control of our business information/systems and this clever tool allows this. It’s really clear and easy to understand, coming with a user-friendly
glossary. You really can be in control of your systems and if you’re a regulated industry, it really is a must to show you are doing all of the necessary compliance measures.
Also, maybe you gave someone access to something for a short period of time, but forgot to revoke this. You will instantly know from this report.
But I use Multi-Factor Authentication, so I’m safe aren’t I?
Multi-factor authentication or MFA as it’s also commonly known is an authentication method where access to systems is granted only after presenting two or more pieces of evidence that you are who you say you are.
The problem with this is that it can give a false sense of security, as outlined below:
- Sometimes this authentication goes to an email and obviously if someone has breached your system, this won’t be very effective. Even if you receive your code through a text message to your mobile phone, there are still ways that hackers are getting around this. Cybercriminals are socially engineering the mobile phone companies into allowing them to clone a victim’s SIM card. So, they then receive a copy of any messages sent to it, which means your MFA code
- Some hackers are even contacting mobile phone customers directly and claiming that they need an MFA code in order to verify the customer’s identity. Once the hacker receives the code, they then change the recovery information on all your accounts. If someone is going to give away their code, there is nothing to stop them except training and monitoring systems, just in case.
- Even if you use an authenticator app to accept your code, there is still a window of opportunity for hackers to steal this. True it is only a 30 – 60 second slot, but do you know if you or your employees have logged in from a coffee shop’s wi-fi, for example? Were they actually on a trusted wi-fi? It is really easy to set up a rogue one and hackers do this specifically to steal trusted information/codes
- We all know we are bombarded with messages every day of our lives. If one of your employees received an MFA request whilst they were in your system, might they just accept it thinking it was because they were accessing the system? Can you be sure? People are always the weakest link.
- Furthermore, cybercriminals are incredibly intelligent and they run a robust business operation – it’s no longer just the teenage kid in his bedroom. They have their fingers in all the pies. It’s only a matter of time before they will find some way to break through MFA. You need to make sure you are monitoring at all times if you want to be safe and in control.
Your Office 365 needs to be as secure as possible
In view of the threat being posed today, you know this is not a nicety, but a necessity. People are the weakest link and you have your staff scattered now. You can’t be everywhere and even if you were, these criminals are really smart, can you be sure you wouldn’t fall for their scams?
365 Protect has given our clients peace of mind that their Office 365 is fully protected, especially during the current situation.
Is your IT provider taking your Office 365 security this seriously?
[/vc_column_text][vc_column_text]
Need help getting making sure your Office 365 is as secure as it can possibly be?
Let’s chat…
[/vc_column_text][stm_post_bottom][stm_post_about_author][stm_post_comments][/vc_column][vc_column width=”1/4″ offset=”vc_hidden-sm vc_hidden-xs”][stm_sidebar sidebar=”527″][/vc_column][/vc_row][vc_row][vc_column][/vc_column][/vc_row]

